Understanding the Slowloris Attack: A Stealthy Web Server Exploitation
In the realm of cybersecurity, there are various forms of attacks that can compromise the integrity, availability, and security of web servers. One such attack, known as the Slowloris attack, operates with a unique approach to exploit web servers. In this article, we will delve into the workings of the Slowloris attack, its impact, and measures to mitigate its effects.
What is a Slowloris Attack?
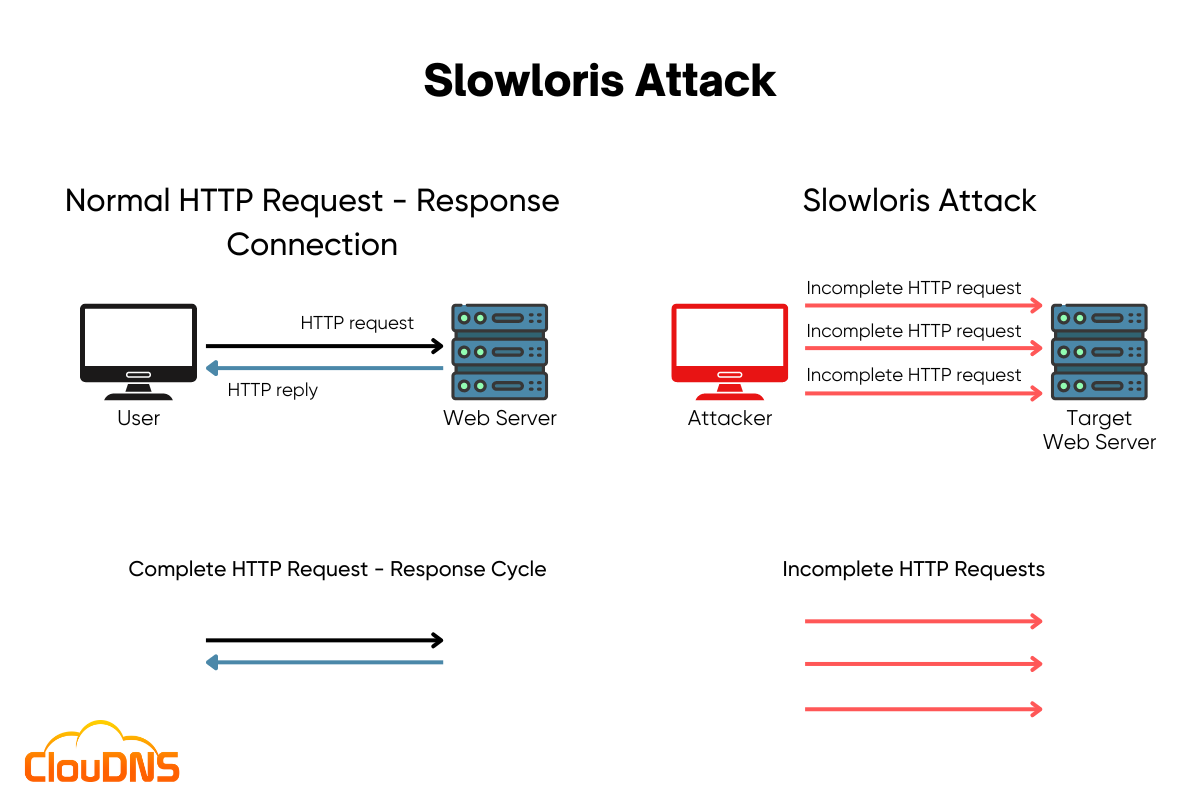
The Slowloris attack is a type of Denial-of-Service (DoS) attack that targets web servers. Unlike traditional DoS attacks that flood servers with a massive volume of requests, Slowloris takes a stealthier approach by exploiting the way web servers handle simultaneous connections. Instead of overwhelming the server with excessive traffic, it aims to exhaust server resources by keeping multiple connections open for an extended period.
How Does Slowloris Work?
Slowloris achieves its goal by utilizing a fundamental characteristic of web servers: the ability to handle multiple concurrent connections. It works as follows:
Initialization: The attacker initiates connections to the targeted web server, typically through multiple threads or processes.
Partial HTTP Requests: Instead of sending complete HTTP requests, Slowloris sends partial requests, keeping the connections open.
Delayed Completion: The attacker intermittently sends additional headers to prevent the server from timing out the connection, thus maintaining the open connections.
Resource Exhaustion: As the server allocates resources for each open connection, Slowloris keeps the connections alive for as long as possible. This gradually exhausts server resources, such as available sockets or maximum concurrent connection limits.
Effects of a Slowloris Attack:
The Slowloris attack can have severe consequences for a targeted web server:
Denial of Service: By tying up server resources, Slowloris can lead to a denial of service for legitimate users, as the server becomes unable to handle their requests.
Scalability Issues: The attack exploits the scalability limitations of web servers, potentially rendering them ineffective even against relatively low traffic volumes.
Difficult Detection: Slowloris is designed to fly under the radar, making it challenging to identify and mitigate the attack promptly.
Mitigating Slowloris Attacks:
Preventing and mitigating Slowloris attacks require a multi-layered approach. Here are some recommended countermeasures:
Implement Rate Limiting: Configure web servers to enforce connection limits per IP address or block clients that exceed a certain threshold.
Load Balancers: Employ load balancers to distribute traffic evenly across multiple backend servers, reducing the impact of Slowloris on individual servers.
Intrusion Detection Systems: Utilize network-based intrusion detection systems (IDS) or intrusion prevention systems (IPS) to detect and block Slowloris attack patterns.
Server Configuration: Optimize server configurations by adjusting timeouts and connection limits to mitigate the effects of Slowloris attacks.
Traffic Analysis: Monitor network traffic patterns and identify any unusual connection behavior, enabling proactive detection and response.
Conclusion:
The Slowloris attack presents a unique challenge to web server administrators due to its stealthy and resource-exhausting nature. By taking advantage of the way servers handle concurrent connections, Slowloris can bring down even robust servers with relatively low traffic. It is crucial for organizations to implement robust security measures, including rate limiting, load balancing, and intrusion detection, to mitigate the risks associated with Slowloris attacks.
By staying vigilant, maintaining up-to-date server configurations, and employing appropriate security measures, organizations can fortify their web servers against Slowloris attacks, safeguarding their availability and protecting the integrity of their online services.


Comments
Post a Comment